Over 90%
of MSPs are NOT compliant. Yet.
With the right cybersecurity compliance management software, you’ll hit the ground running.
Get Compliant
Once you’re compliant, don’t stop. Use that knowledge to expand your services.
Sell Compliance
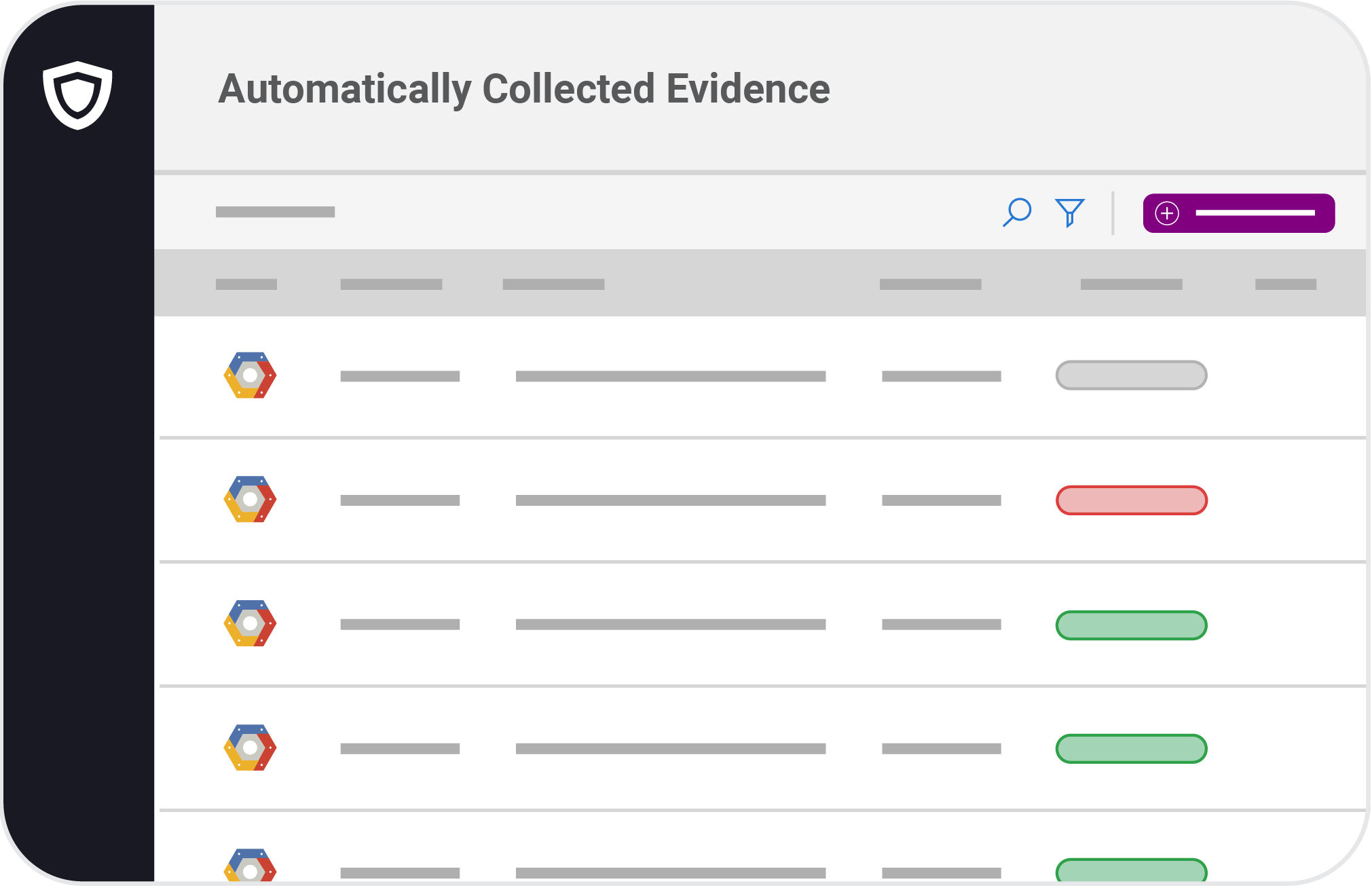
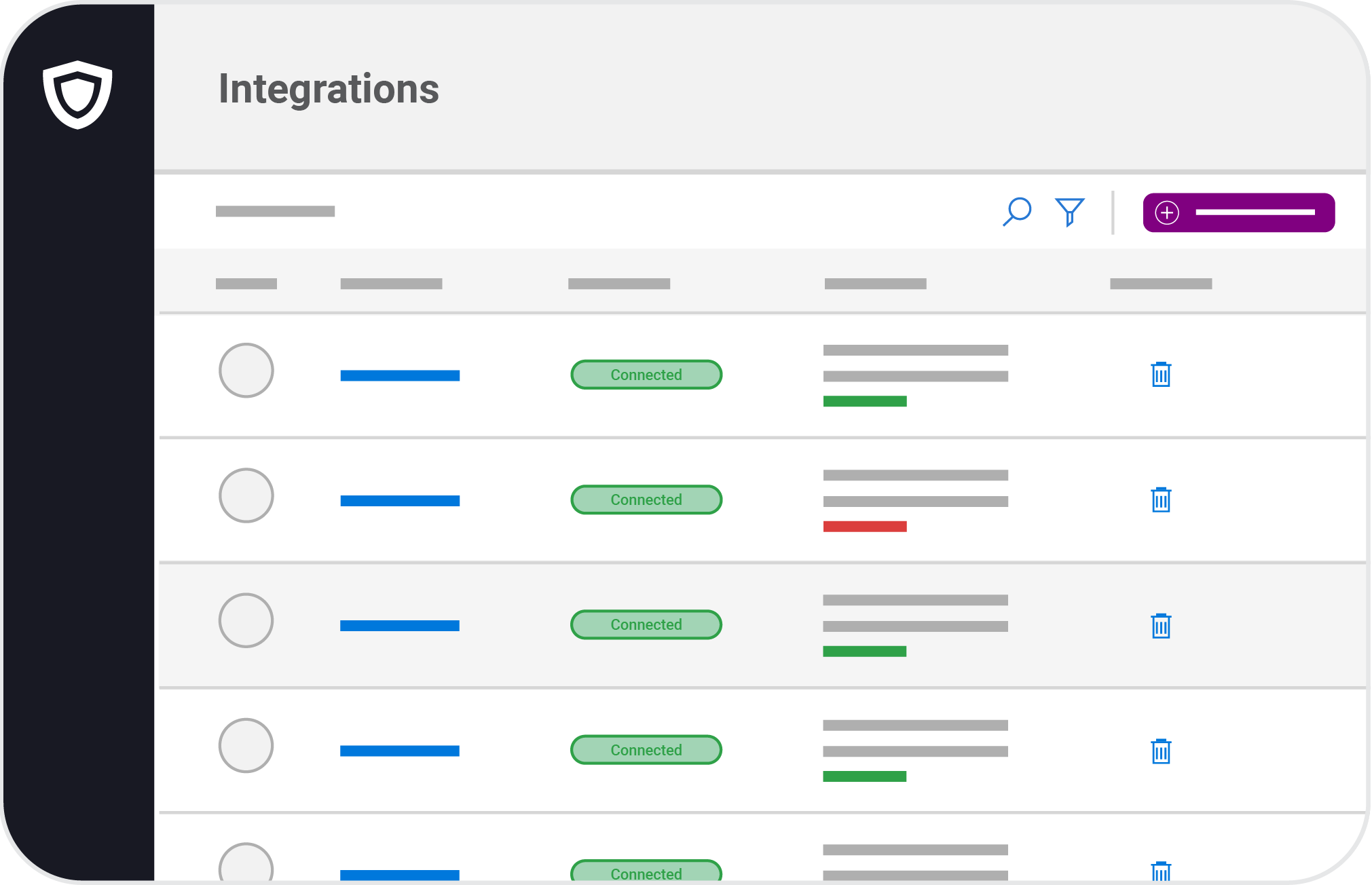
Be continuously compliant by connecting and monitoring 35+ systems such as AWS, Azure, Office 365, and many more.
See All Features
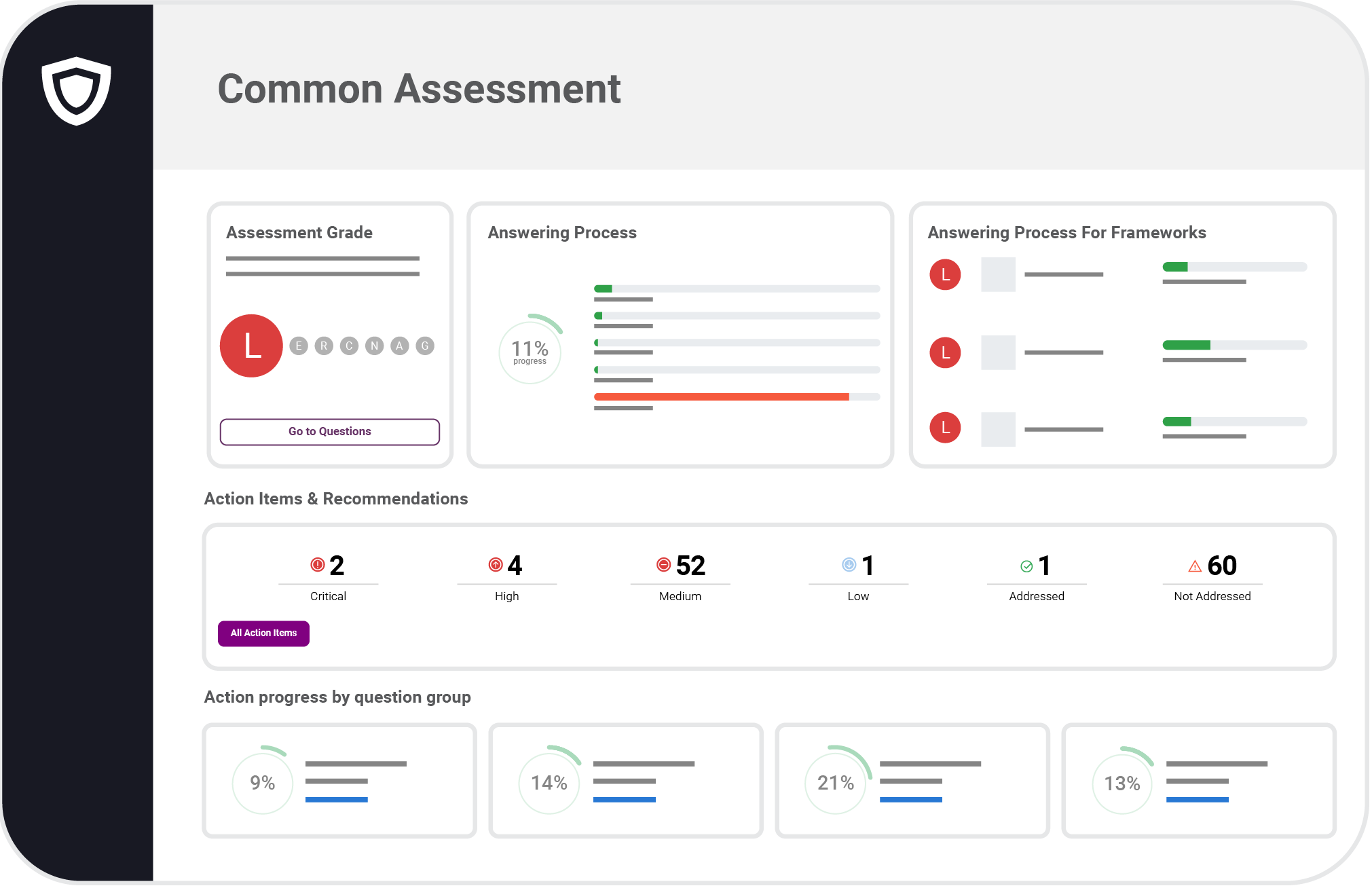
Start with customizable, expert-verified templates. Cross mapping finds the overlap between common standards to get you cruising through compliance tasks.
See All Features
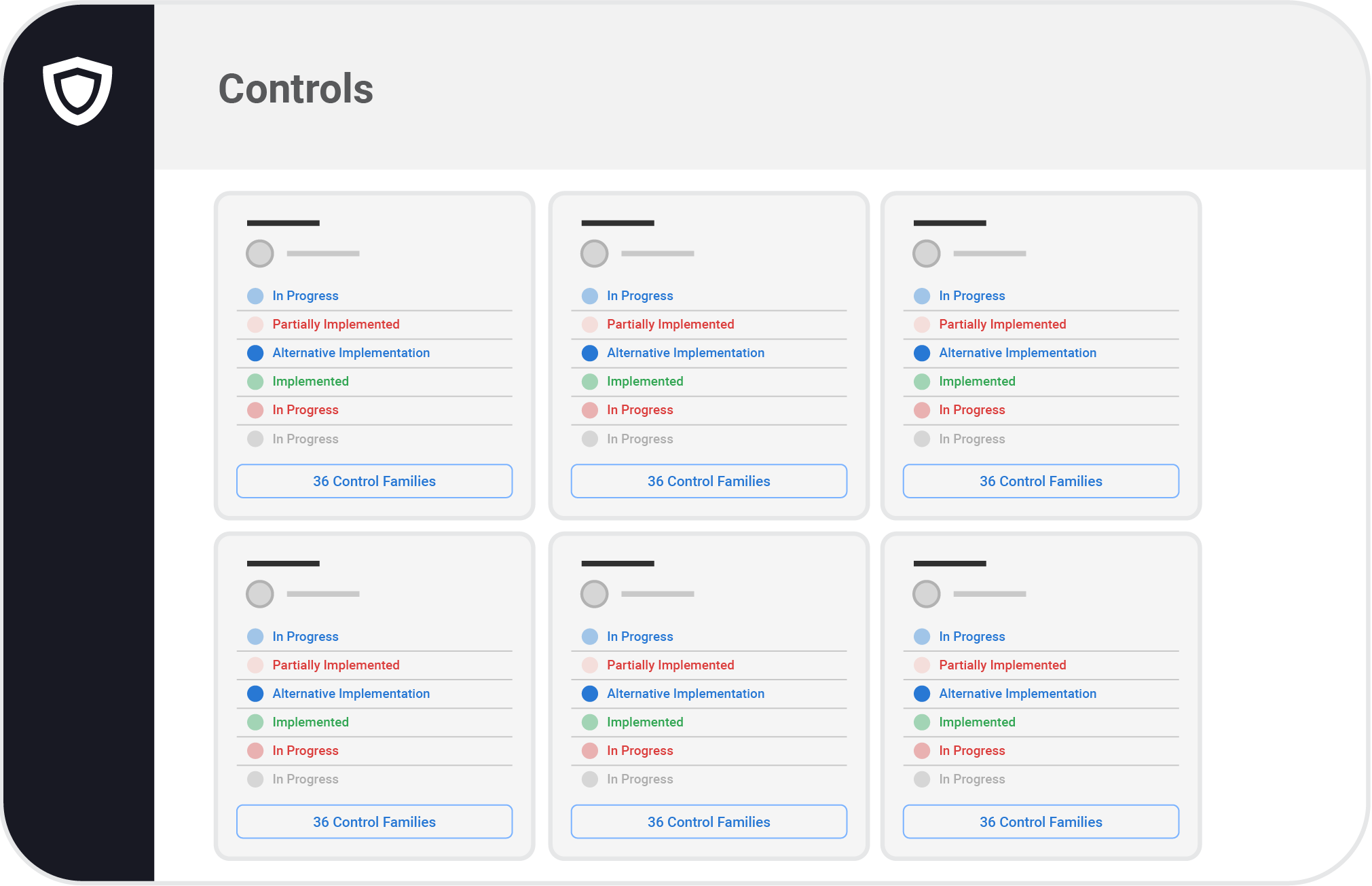
Managing evidence and policies keeps everything at hand. Keep tabs on risks and vendors too. No more spreadsheets and scattered documents.
See All Features
Everyone on the team needs to contribute to compliance. In this personalized portal they can access policies and handle any tasks they need to do.
See All Features